|
|
Microsoft Bug Up For Auction on EBay
Posted by Pile
(10433 views) |
  |
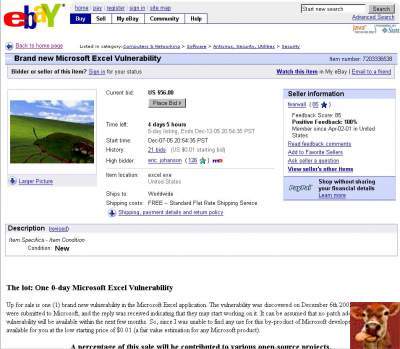 In an amusing jab at Microsoft and their lackluster ability to promptly identify and fix vulnerabilities in their software, an IT guy has placed up for auction on eBay "One 0-day Microsoft Excel Vulnerability". In an amusing jab at Microsoft and their lackluster ability to promptly identify and fix vulnerabilities in their software, an IT guy has placed up for auction on eBay "One 0-day Microsoft Excel Vulnerability".Interestingly enough, eBay had the auction pulled, meanwhile they let several other auctions run where people misled others by selling an empty XBox360 carton. | |
eBay auction listing: The lot: One 0-day Microsoft Excel Vulnerability Up for sale is one (1) brand new vulnerability in the Microsoft Excel application. The vulnerability was discovered on December 6th 2005, all the details were submitted to Microsoft, and the reply was received indicating that they may start working on it. It can be assumed that no patch addressing this vulnerability will be available within the next few months. So, since I was unable to find any use for this by-product of Microsoft developers, it is now available for you at the low starting price of $0.01 (a fair value estimation for any Microsoft product). A percentage of this sale will be contributed to various open-source projects. Vulnerability Description (read carefully, this is what you bid on). Microsoft Excel does not perform sufficient data validation when parsing document files. As a result, it is possible to pass a large counter value to msvcrt.memmove() function which causes critical memory regions to be overwritten, including the stack space. The vulnerability can be exploited to compromise a user's PC. It is feasible to manipulate the data in the document file to get a code of attacker's choice executed when malicious file is opened by MS Excel. The exploit code is not included in the auction. You must have very advanced skills if you want to further research this vulnerability. What will be delivered (at no extra charge): The winning bidder must provide an e-mail address that accepts .xls attachments. Two xls files will be mailed to this e-mail address: one file is the original Microsoft Excel document, the other one is a copy of the same document modified to demonstrate the vulnerability. The demonstration merely triggers the exception causing Excel to crash. It does not do anything malicious. A detailed description of the vulnerability will be provided in the message body. At that time you can claim youself to be THE ONLY ONE IN THE WORLD possessing the knowledge about the vulnerability. Wow! Imagine that! (Well, not counting Microsoft, but I really doubt that they'll share it with anyone.) It is up to you what to do with it, but you may not use it for malicious purposes - see terms and conditions below. Special offers: Microsoft representatives get 10% off the final price. To qualify, you MUST provide @microsoft.com e-mail address and MUST mention discount code LINUXRULZ during checkout. | |
| 1 Article displayed. |


 Bumper Sticker Store
Bumper Sticker Store



